
[ZAFL] Some Settings
두비니
·2022. 1. 11. 01:46
논문을 읽고 사용해보는 중입니다
https://www.usenix.org/conference/usenixsecurity21/presentation/nagy
Breaking Through Binaries: Compiler-quality Instrumentation for Better Binary-only Fuzzing | USENIX
Open Access Media USENIX is committed to Open Access to the research presented at our events. Papers and proceedings are freely available to everyone once the event begins. Any video, audio, and/or slides that are posted after the event are also free and o
www.usenix.org
1트 : Docker를 이용한 ZAFL 사용법
사용 방법 : https://git.zephyr-software.com/opensrc/zafl#installation-from-docker-recommended
Open Source Software / zafl
Zipr-based AFL collaborative group
git.zephyr-software.com
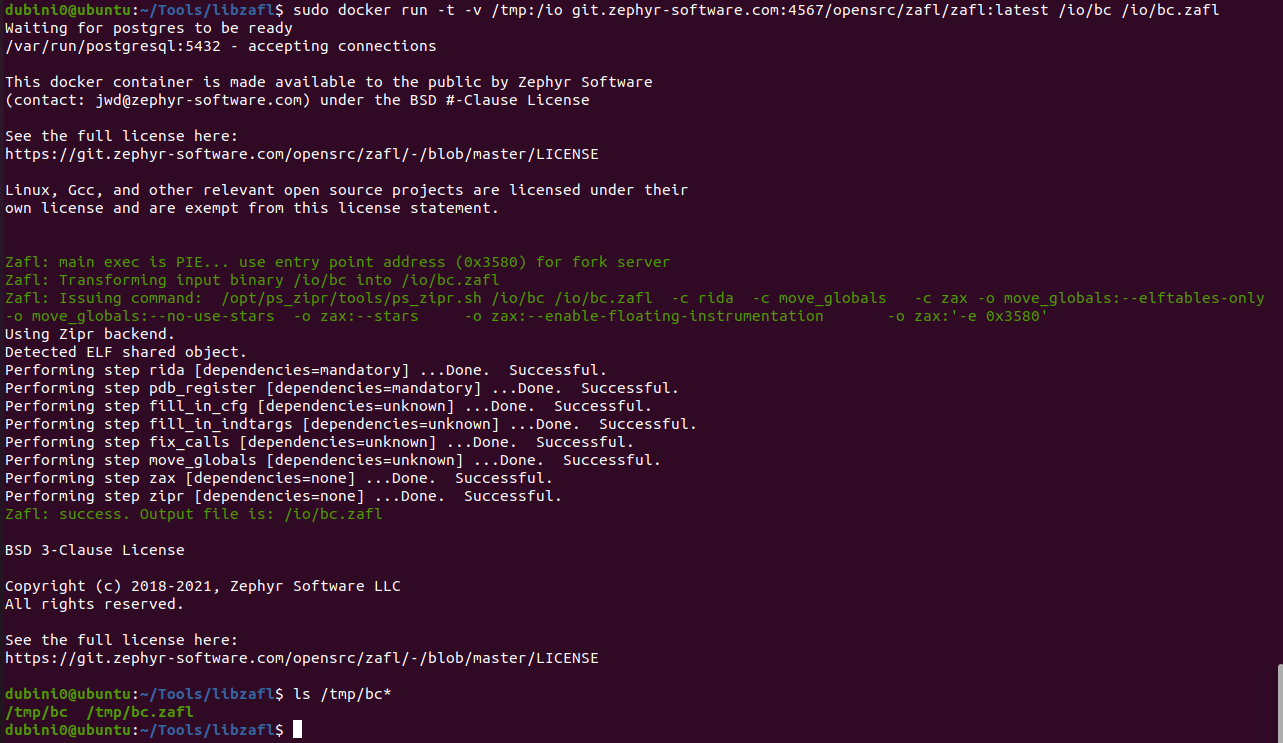
zafl 기반으로 fuzzing 돌려보기

2트 : 직접 빌드하여 ZAFL 사용하기
필요한거 : Zipr, link : https://git.zephyr-software.com/opensrc/zipr
Open Source Software / Zipr Toolchain
GitLab Enterprise Edition
git.zephyr-software.com
installation link : https://git.zephyr-software.com/opensrc/zafl#installation-from-source-for-developers
Open Source Software / zafl
Zipr-based AFL collaborative group
git.zephyr-software.com


큰 과정
IR(Intermediate Representation) Extraction -> ZAX Tranform -> Binary Reconstitution
- IR은 Zipr이라는 binary rewriting process에 맡김 (정확히는 IR data structure을 뽑아냄)
- 이후 ZAX Process를 통해 4가지 Transform을 진행
- 마지막으로 Zipr로 다시 Binary Reconstitution을 진행하여 binary rewriting 수행
+) Steps
- rida
- pda_register
- fill_in_cfg
- fill_in_indtargs
- fix_calls
- move_globals (여기까지 모두 Zipr 몫)
- zax
- zipr (Binary Reconstitution 부분)
논문 정리글도 추후에 공개할 예정
'SYSTEM HACKING' 카테고리의 다른 글
| Windows API Basics (0) | 2023.04.15 |
|---|---|
| [Cheat Engine] 기본적인 사용법 / 단축키 (0) | 2022.01.25 |
| [IDA] 동적디버깅 setting (0) | 2021.07.23 |



